Gather Achieves ISO 27001 Certification
What is ISO 27001?
ISO 27001 specifies the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS), within the context of the organisation.
It also includes requirements for the assessment and treatment of information security risks tailored to the needs of the organisation.
Why ISO 27001?
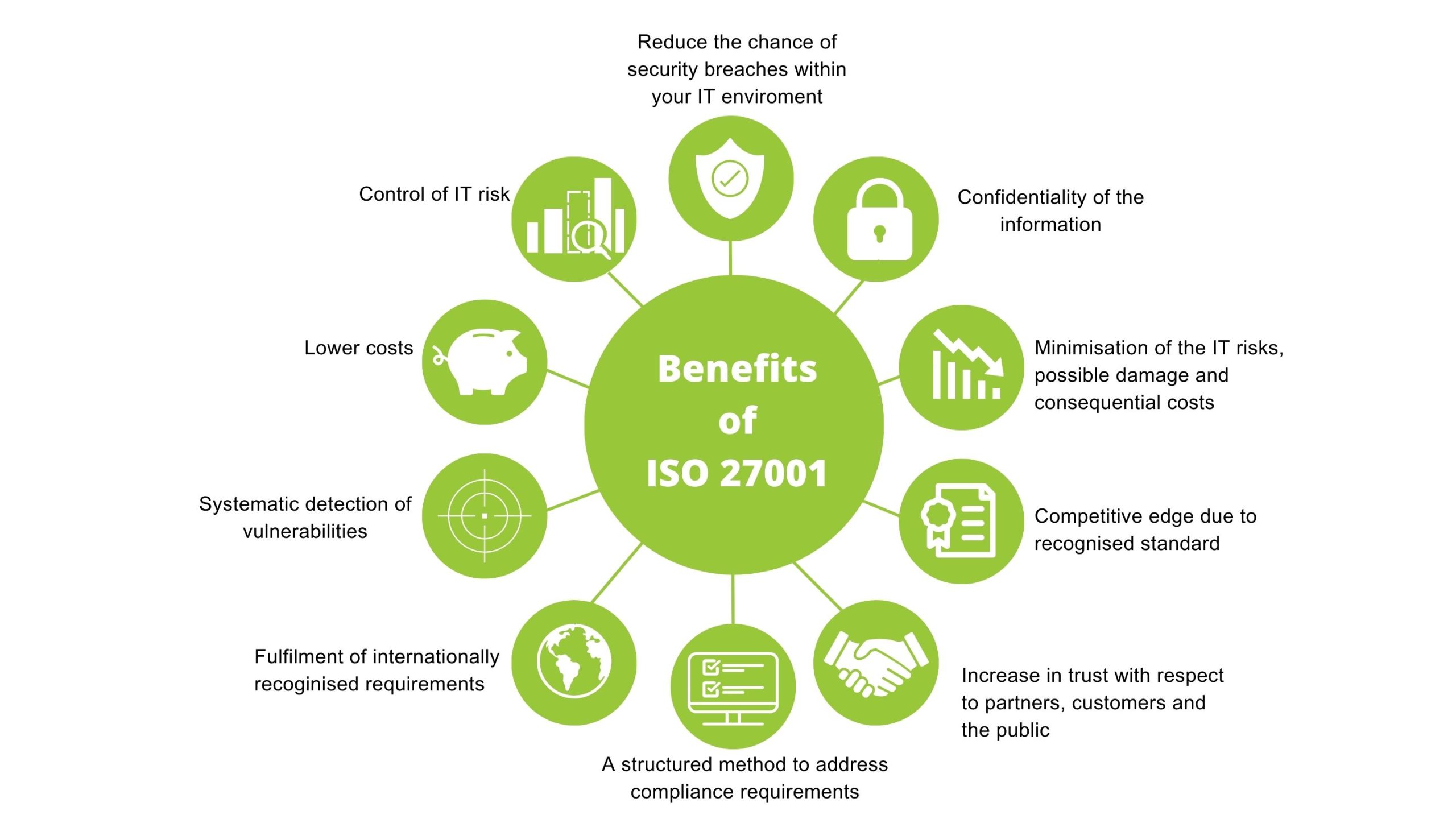
ISO 27001 ensures that cyber security is implemented and maintained so that both our data and our client's data are kept confidential.
It does so with the ISMS - a framework that allows for constant review and resultant improvement but is flexible to the business needs by providing:
- Improved data security
- Mitigation of breaches by addressing risk
- Continuous improvement with PDCA
- Credibility
How to achieve ISO 27001?
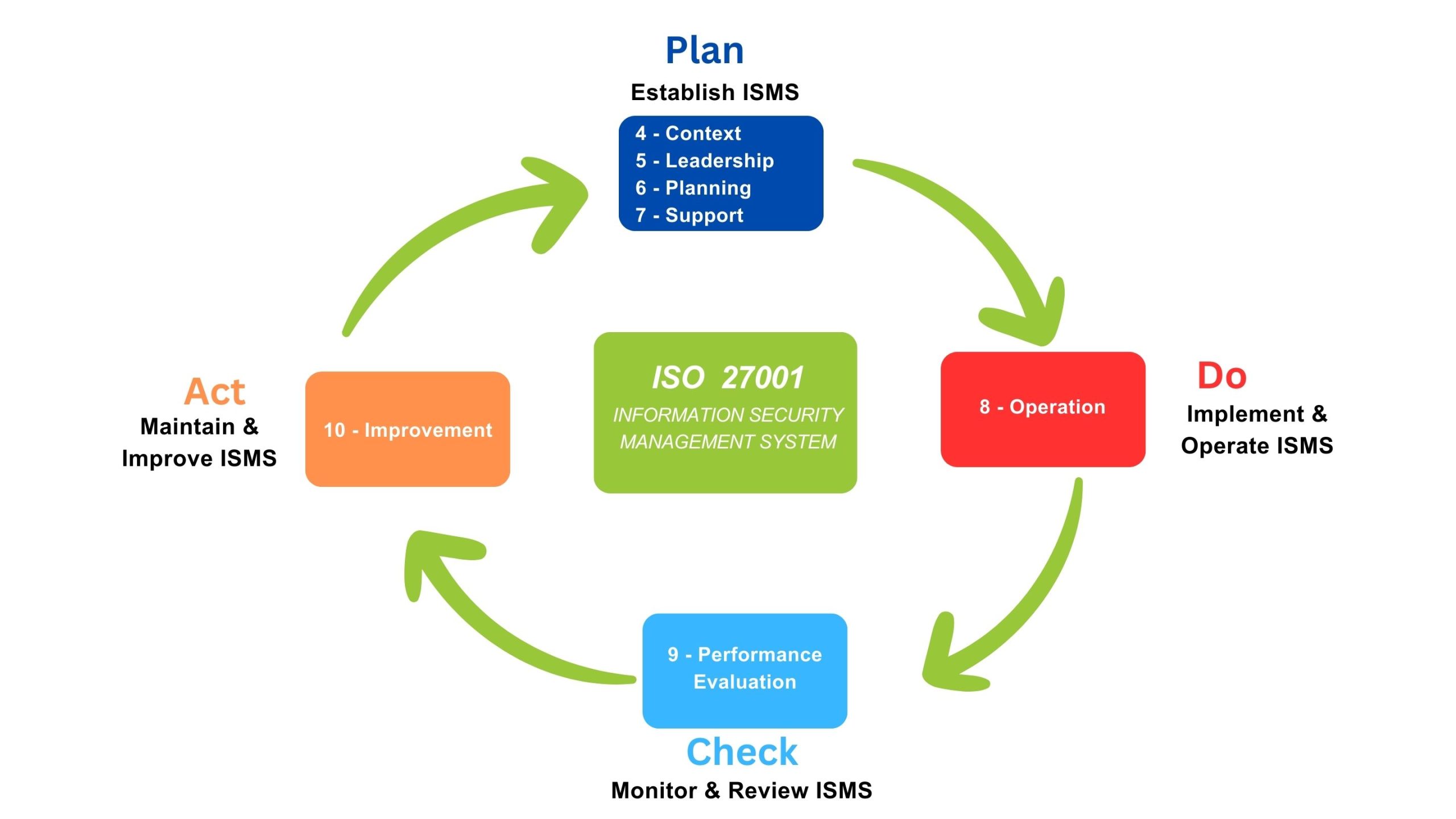
It’s a five-step process to become certified and an integral part of an ISO certified management system is that there must be continuous improvement.
- Gap analysis
- Manual of Operation
- Staff Training
- Internal audit
- External audit
When you finish painting the Forth Bridge you start again at the beginning!
We started out by documenting our best practices and daily operating procedures, describing what and how we do things.
For example, we need to explain that we make a cup of tea because we're thirsty and because we like it…
Our policies and procedures need to support the standard stipulated by ISO 27001. There was a need for us to subtly tweak the way we work to do so. However, the standard is not meant to be restrictive. It is a flexible framework that ultimately should fit our business.
With a management system defined, awareness training around the system took place, which effectively emphasised why we are taking the sanctity of our own and our customer's data seriously.
At this point, we needed to be happy that our system and its controls work as we expected by doing some internal audits, following the next step, which is the scary bit, where we’re audited by an external auditor!
All’s well that starts well, and whilst ISO is iterative and the continuous improvement process of 'plan do check act', now just keeps rolling. The really exciting bit is we have received a lush certificate for the wall!

Enjoyed these tips?
Click HereIf you found this blog helpful, we have lots of other useful downloads with tips on using technology to improve your business. Browse our white papers, guides and free policy templates below.





